.jpg)
We use passwords every day - sometimes perhaps not the most secure ones. Yet using them securely can prevent a lot of trouble in the long run. With the vast amounts of sensitive data we now have, our digital identity has become too important to entrust to just one or a few passwords.
Should a password be compromised, i.e. fall into the wrong hands, only a small digital partial identity should be affected by this incident.
Am I already affected?
Many people are probably familiar with the emails asking you to change your password after an attack on your online service provider. Questions like "Where else have I used this password?" can ideally be answered with a "Nowhere".
With services like Have I been Pwned? by Troy Hunt or the HPI Identity Leak Checker dby the Hasso Plattner Institute can be used to search for past data leaks for an email address. Have I been Pwned? can also be used to check whether a password has already been leaked and is therefore considered insecure. If you do not want to submit your password online to Have I been Pwned?, you can alternatively download the entire encrypted password database with SHA-1 or NTLM hashes ( haveibeenpwned.com/Passwords) and check locally for occurrences of your own passwords.
What makes a secure password?
Over time, some methods for creating and keeping passwords have proven themselves. Basically, a password is only good if it is as random as possible. This is called the entropy of a password. If parts of a password are a logical sequence, this reduces the entropy of the password. For example, words found in a dictionary or numerical sequences of calendar dates are not secure password components.
For the highest possible password security, the characters it contains should come from the largest possible data space. A 4-digit password consisting of numbers has only 10,000 possible combinations. If lower case letters are added, there are already 1.6 million. Mixed with capital letters, almost 15 million passwords are possible. If the password also contains special characters, the possible number of 4-digit passwords multiplies to over 81 million.
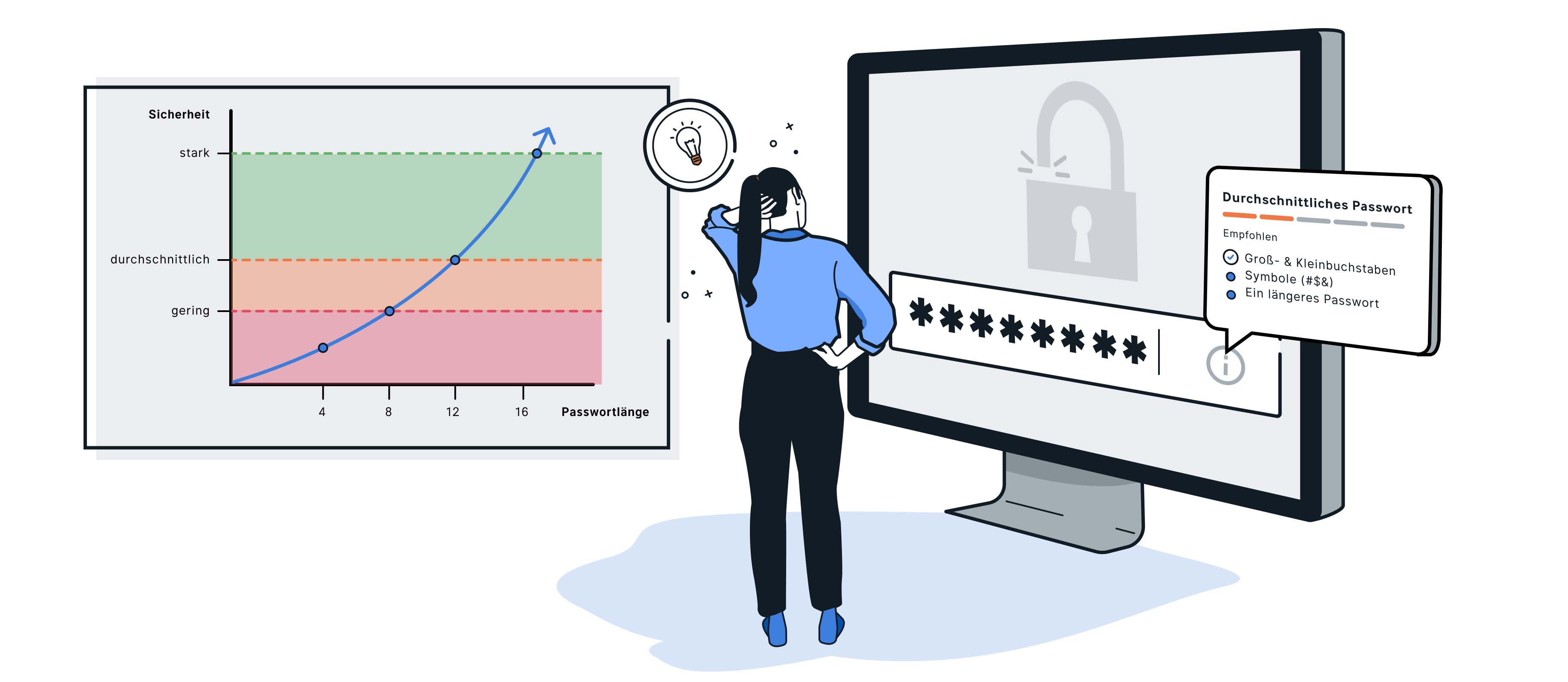
The more password combinations possible, the longer it takes to decrypt a password in the event of an attack. That's why we recommend using passwords that are as long and random as possible.
But how long is long enough? To be on the safe side, it is advisable to choose a password with 12 characters or longer from a combination of upper and lower case letters, numbers and special characters.
Methods for creating secure passwords manually
In order to think up a password that is as secure as possible, it helps to create a secure pattern that is known only to oneself.
Such a pattern can be, for example, a sentence you have thought up yourself, which is then supplemented with special characters and numbers. The first letters of the words and special characters then form the password.
Example:
Today I think up my 1st secure password using this method.
TItum1stsputm.
If this password is extended by further special characters, it has a very high entropy and is therefore particularly secure. You don't have to limit yourself to sentences, but can also use haikus or other short poem forms.
Methods for automatic password generation
But even with such a creation tool, it is difficult to generate individual passwords for each service that are sufficiently different from each other and thus actually secure.
A password manager can take a lot of the work out of this - both in creating secure passwords and in managing them. Today, simple password managers are already integrated into every common web browser. The advantage here is the ability of the browser provider to use cloud synchonisation. However, this can also be seen as a disadvantage, as access to one's entire digital identity is entrusted to a foreign cloud. Furthermore, simply filling in credentials for non-browser applications becomes difficult.

A good alternative is a dedicated password manager. Popular password managers include KeePassXC/KeePassDX and 1Password. The applications can be installed on all common devices and store the passwords in encrypted database files. To open these databases, a master password is used, which should be as secure as possible. Via plug-in, web browsers can communicate with the password manager and offer the corresponding access data on individual websites for automatic completion.
In order to synchronise access data between several devices, however, the database file must be available on all devices. This in turn can be synchronised via a cloud, for example. The chosen master password helps to maintain the security of the stored passwords in case the password database should fall into the wrong hands.
How do we work?
We naturally also have to deal with password-protected applications in our daily business. In addition to the greatest possible security, it is also important for us to remain efficient and not to slow down processes with unnecessary hurdles. Therefore, in some of our projects, the use of a dedicated password manager has proven its worth. With this, accesses that are valid for several web services can easily be added to the access data entry with their URLs. Thus, when changing the password of the account, it is not necessary to edit a separate entry for each URL. In addition, this dedicated password manager also allows us to generate tokens for two-factor authentication (2FA), thus providing even more security.
Those are our tips and hints for users for now. More information is available from the German Federal Office for Information Security (BSI). In addition, we already have another blog post in the works in which our Security Xperts deal with the topic of access protection in application development.
Data Science
Learn more about our services